SecuriOT Live
Webinar on privileged remote access and how SecuriOT and BeyondTrust can enable secure access to your manufacturing floor and production IT.
We will show you, how to securely provide remote access for “classic” OT use cases such as:
- A technician needing to make changes on a SCADA server (e.g. GE iFix)
- A technician needing access to a specific PLC to make changes (e.g via Step7 or Machine Edition)
- A Service Provider doing maintenance tasks in OT specific applications (such as back-up & versioning software VersionDog from Auvesy)
In addition, you will hear how to find inspiration and guidance from standards such as IEC62443 or the NIST framework to enable you to tie technologies into the daily work around cyber security.
Webinar about Moving OT Applications to the Cloud – Risky Business?
Initiatives such as digitization & Industry 4.0 are driving interest for and adoption of cloud services. Initially as repository for measurement data, but recently even “hardcore” ICS/OT applications come as cloud-only.
How does that impact your security posture for the crown jewels of your business?
Webinar on cyber security threats against OT infrastructure
Attacks on OT infrastructure is exploding by 2000% YoY as per the latest IBM X-Force Threat Intelligence Report Index.
SecuriOT is specialized in OT cyber security and or key technology partners at FireEye and Nozomi Networks have partnered together to offer industry-leading visibility, monitoring and protection for OT systems.
We will give you inspiration on these aspects:
- Risk Based Assessment – How to justify cyber security investments?
- Creating visibility of OT-infrastructure – if you can’t see it, you can’t protect it
- Threat intelligence and “readiness”– how to use threat intelligence in daily Cyber Security work?
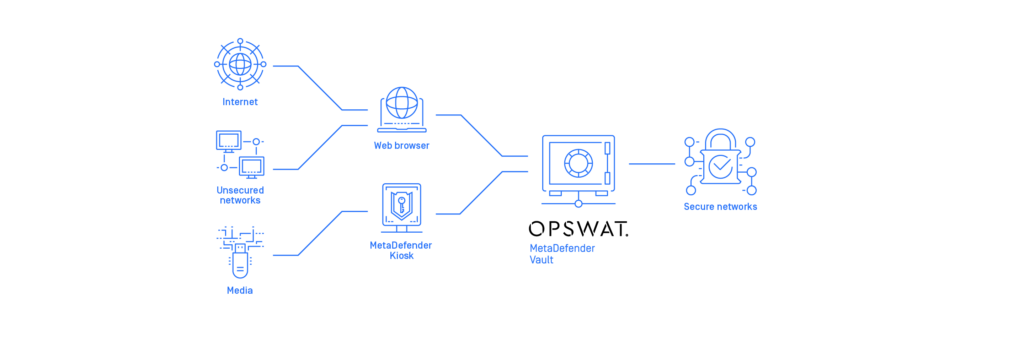
In this webinar we focus on one of the biggest threats against OT environments: Unsecure File transfer from an untrusted network to your critical control systems & infrastructure
The digitization of OT systems requires an increased connectivity for e.g. 3rd party support or file transfer for updating systems and dataflows. It opens doors that normally were closed.
The webinar will have a two-folded focus:
- How can security standards guide you to mitigate this risk?
- How can technology from OPSWAT help you with a layered approach to ensure system integrity and malware protection?
Watch this webinar for inspiration on how to handle this threat both from a process & technology perspective.