IEC 62443 – A security standard for automation- and production systems
”Defence-in-depth” – focus on both the security process and the technology
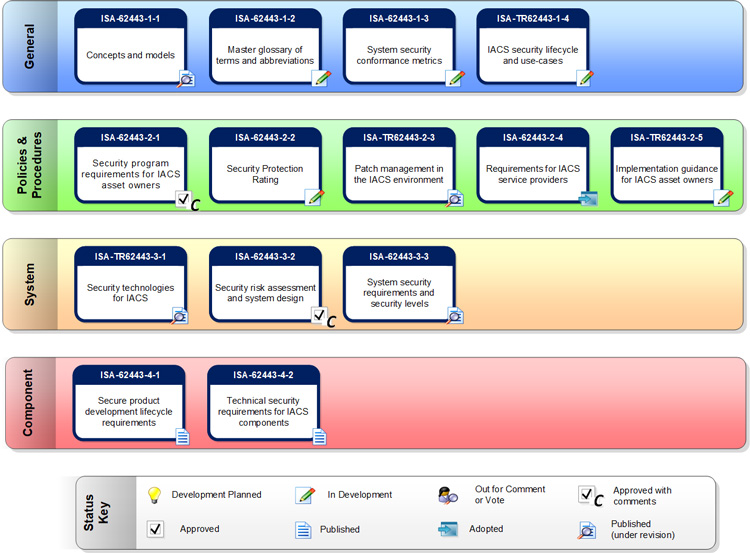
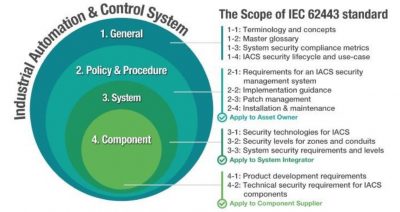
A total of 9 standards and 5 technical documents that constitute the framework for IEC 62443. These work in accordance with two superordinate principles:
The 7 Foundational Requirements are technical areas and precautions that the OT-infrastructure has to work with:
- FR 1 Identification & authentication control
- FR 2 Use control
- FR 3 System integrity
- FR 4 Data confidentiality
- FR 5 Restricted data flow
- FR 6 Timely response to events
- FR 7 Resource availability
4 Security Levels that describe the desired functionality and security standard. This is juxtaposed to the risk that is identified by the company:
- SL1 – Protection against the “coincidental” attack.
- SL2 – Protection against the targeted attack conducted with simple methods, few resources, low technical insight, and low motivation.
- SL3 – Protection against the targeted attack conducted with sophisticated methods, limited resources, and moderate technical insight and motivation.
- SL4 – Protection against the targeted attack conducted with sophisticated methods, many resources, high technical insights, and a high degree of motivation.
For each of the 7 Foundational Requirements, the standard propounds advice and recommendations to technical implementations that are applied in the OT-infrastructure in achieving the respective Security Levels. This is primarily addressed in 62443-3-3.
These technical suggestions are not specific to a particular product, technology, or supplier, but more generic concepts that are applied to heighten security levels in the OT-infrastructure.
Where are these standards obvious to use?
The different documents and standards will provide recommendations for utility- or production companies in working towards securing their OT-infrastructure:
- Organization of security (62443-1-1, 2-1, 2-2 & 2-4)
- Management of vulnerabilities and patching in OT-infrastructure (62443-2-3)
- Methods for completion of risk-assessments of OT-infrastructure (62443-3-2)
- Implementation of technical precautions in OT-infrastructure (62443-3-1 & 3-3)
- Requirements for certification of products with regards to security functions (62443-4-1 og 4-2)
Why should you use IEC/ISA 62443?
- This frame of reference focuses on threats and risks to OT-infrastructure.
- It works from the premises of how cybersecurity should be handled in OT-infrastructure.
- A generic approach to OT-security that is independent of technology platforms.
- It offers tangible advice and focus areas that can be utilized in all business sizes.

SecuriOT sees this frame of reference as a central component in consulting and risk assessing our customers.
We are member of the ISA and are continually keeping ourselves updated via courses and webinars for us to provide customers with the best possible advice.
The ISA has devised a document that provides an overview of the standard and its advantages. Fill out the formula on the right to download this document.

The ISA/IEC 62443-series of standards. Developed by the ISA99- committee (https://www.isa.org/isa99/) who offers a flexible framework to address and manage current and future security vulnerabilities in the so-called Industrial Automation & Control Systems (IACS).
The committee is in thorough international collaboration with security experts from the IACS to develop standards that are pertinent to all industry sectors and critical infrastructure.
