
Nozomi’s Guardian provides your company with these advantages:
- Time savings in relation to asset management and keeping track of devices in your production system.
- Real-time overview and great visibility
- Efficient risk assessment with regards to vulnerabilities in the production system
- Remote collection of data from smaller location or segmented networks
- Great reporting possibilities regarding standards and compliance
- “Smart Polling” for active scanning of e.g. Windows OS to gather OS-information and detection of USB-usage
- “Threat Intelligence” regarding newly detected threats and attack patterns against OT-infrastructure
- Access to a comprehensive “vulnerability repository” – updated information about specific vulnerabilities which can be found on the components in your OT-infrastructure
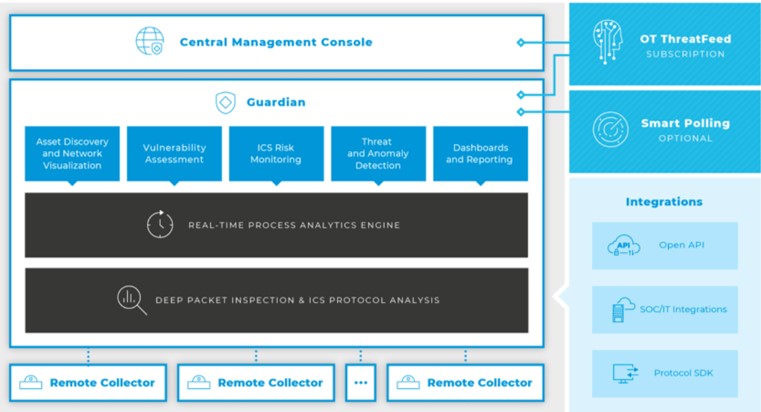
Guardian have gathered their primary functions in one solution which have the following advantages:
- Asset tracking – a continually updated overview
Guardian conducts “deep packet inspection” through the 1-7 levels in the OSI protocol stack. That means that the solution can depict an elaborate picture of production systems’ infrastructure and identify protocols and the devices’ infrastructure (including supplier, types, etc.). When utilizing asset tracking, companies constantly have an updated image of devices in the infrastructure and are hereby sparing resources on manually updating databases.
- Remote Collector
Remote Collector is a “probe” that is capable of gathering detailed information about the ICS-environment from smaller production locations. Previously a comprehensive solution had to be installed on smaller production locations, but this is not necessary with Nozomi’s Remote Collector. A Remote Collector gathers data from the location and sends it to the Guardian which is placed in a central location. In doing so, the Guardian can analyze this data from remote locations. Remote Collector can also be utilized via larger ICS-infrastructures on one location which is segmented through VLAN and/or NAT. Remote Collector can be delivered both as a virtual image or as hardware.
- IT and OT Protocol Baselining – visualization of the network
Guardian can analyze a range of protocols and attributes from the leading products for ICS Systems. An excerpt of these:
OT-protocols and applications:
- Aspentech Cim/IO, BACNet, Beckho ADS, BSAP IP, DNP3, Enron Modbus, EtherCAT, EtherNet/IP – CIP, Foundation Fieldbus, Generic MMS, GOOSE, Honeywell, IEC DLMS/COSEM, ICCP, Modbus/TCP, MQTT, OPC AU, Siemens CAMP, Mitsubishi Melsoft, Mitsubishi SLMP, ABB Totalflow, etc.
IT-protocls and applications:
- BROWSER, CDP, DCE-RCP, DHCP, DNS, DRDA, FTP, FTPS, HTTP, HTTPS, ICMP/PING, IGMP, IKE, IMAP, IMAPS, Kerberos, KMS, LDAP, LDAPS, LLDPMDNS, MS SQL Server, MySQL, NetBIOS, NTP, OSPF, RDP, etc.
See the full list of protocols here: https://www.nozominetworks.com/downloads/US/Nozomi-Networks-Protocol-Support-List.pdf

- Continuous monitoring – Warning about vulnerabilities and changes in the infrastructure
When the solution is incorporated and the traffic is baselined, the Guardian will be able to warn on different incidents:
- Increased traffic in relation to normal patterns
- New protocols from other devices
- New devices or IP-addresses that enters the network
- PLC-equipment which runs other commands than normal
Advanced techniques are utilized, such as Artificial Intelligence and Machine Learning to detect and warn of unusual traffic.
- Minimization of time spent on troubleshooting and analyzing security incidents
The overview of the “real-time” information, which the technology the Guardian offers, enables your company to react faster and more efficiently. That means that downtime is minimized and thus minimizing the consequences of an incident. Correspondingly, the reporting of an incident is easily accessible through a reporting module and dashboards in the solution.
- “Smart polling” – active scanning of Windows Servers
ICS-environments have numerous Windows components running and it is often a specific goal for hackers and malware, but this component is not included in the same update-cycle as IT. It is therefore important to watch the vulnerabilities that the OT-server platform is facing. “Smart Polling” is an active scanning feature that enables the delivery of more information about hotfixes, patches, etc., and thus enables the provision of specific information about which vulnerabilities the client has to respond to. “Smart Polling” can also detect USBs that are used in the server itself. “Smart Polling” is an add-on to Guardian.
- Integration to IT-security system with SIEM and firewalls
Guardian have different options in sending information for both SIEM and firewalls. Nozomi is in a working relationship with IBM Qraddar, Splunk, Arcsight, and LogRytherm to create a comprehensive overview of log information and incidents – both in the IT- and ICS environment. Nozomi has also entered a strategic cooperation with e.g. Cisco, HP Clearpass, Fortinet, and Palo Alto which entails firewall configurations being changeable according to the alarms that the Guardians dispatches.
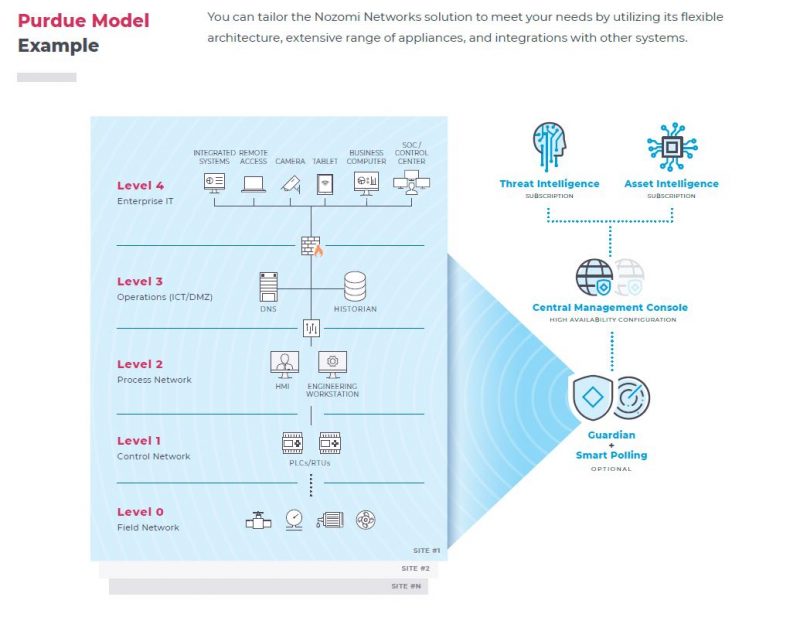
- Flexible architecture with central management with CMC and Guardian units
The Guardian sits on the ICS network and collects a range of detailed information about the network, vulnerabilities and active devices in the ICS network. It is passive appliance, which sits on a “mirrored” port on one or more switches in the production network. Guardian is delivered either as a physical appliance or as a virtual appliance that can be installed on both Hyper-V, KVM, VMware and XEN platforms, and licensed by number of nodes, throughput and number of monitor ports.
- Central Management Center (CMC)
Nozomi also offers a central management platform, which allows for an overall overview of larger installations and perform the essential tasks from a central team. Rights management is offered so that certain persons responsible for a production facility have only the opportunity to manage this part of the entire Nozomi infrastructure.
Willing to try the Guardian solution in your infrastructure?
SecuriOT offers a “Proof of Concept” course where we integrate the solution for three weeks in your infrastructure. Afterward, the results from the course are presented along with tangible recommendations.
Please contact us for more information


