

BeyondTrust Cybersecurity Survival Guide 2022
Get 7 security strategies to protect your data from the biggest risks
This guide includes:
- Research data for insight into how the attack surface changes
- Analysis of how the attackers’ “path of least resistance” moves
- A review of several of the past year’s most sensational security breaches and how they could have been disarmed at several stages in the process
- Survival tips so you can adjust security, close gaps and reduce risk .. while continuing to achieve business optimization and benefits
All companies with OT installations need to provide internal and external technicians with remote access to their systems
Are you also struggling with secure and controlled remote access to your OT environment?
- Do you also lack insight into who, what and when something is done on your systems? And maybe even WHY?!
- For many, it is a great challenge to keep track of both the security and the documentation in connection with a privileged remote access solution.
- In this document from BeyondTrust, you can see a few of the points that you should definitely consider when assessing and establishing solutions to this need.
BeyondTrust is probably best known for their PAM solution, where they again this year have been proclaimed “leader” by Gartner in their PAM Magic Quadrant 2020.
At SecuriOT, we are mildly enthusiastic about both their Privileged Remote Access (PRA) solution and their Endpoint Privilege Management.
No matter how far you as a company have come in OT cyber security, most people face two challenges in particular:
- Managing remote access for external (and often also internal) technicians who need to service devices on the OT network often via specific and proprietary software (eg SCADA servers or PLCs)
- Protection of their endpoints / devices on the OT network, e.g. SCADA or development software servers (Siemens Step7, GE Machine Edition, etc.)
These two challenges solve BeyondTrust in both a secure and flexible way
- Secure Remote Access (Privileged Remote Access)
- Superb control and security of remote access with i.a. full audit trail built-in, and with the highest level of flexibility for the business .. without the use of VPN
- Enables 3rd party / service technician remote access to e.g. OT infrastructure with:
- Fine-granulated control of access
- Full documentation of the technician’s work (audit & compliance)
- Support for proprietary protocols & platforms, e.g. for OT development software and PLCs
- Endpoint Privilege Management
- Stop attacks by removing extended privileges on Windows, Mac, Unix, Linux, and network equipment
“We are proud to have forged a strong partnership and fostered new customer relationships with SecuriOT. Their extensive expertise and knowledge of the OT sector coupled with BeyondTrust’s capabilities and market leading Privileged Access solutions has enabled us to build a strong market presence together across the Nordics. We are excited to see what the future holds for our partnership and look forward to continuing to help OT customers across the Nordic region solve their security challenges alongside the SecuriOT team.”
Alexis Serrano
EMEA Channel & Alliances Director
If you want more information or a demonstration, reach out to us here: mail@securiot.dk

Fill out the formular to get access to BeyondTrust Whitepapers
Error: Contact form not found.
Global leader within Universal Privileged Management
BeyondTrust is among the world leaders in Privileged Access Management, which more than 20,000 customers globally clearly emphasize.
With their market-leading portfolio of products, attacks and cyber-security incidents based on stolen user login, abuse of rights and compromised remote access are prevented.
The BeyondTrust platform makes it possible to easily manage the security around user rights in relation to e.g. endpoint, server, cloud, DevOps & network.
With BeyondTrust, the visibility and control necessary to reduce risks, comply with compliance requirements, and at the same time ensure operational flexibility and performance are achieved.
Universal Privilege Management
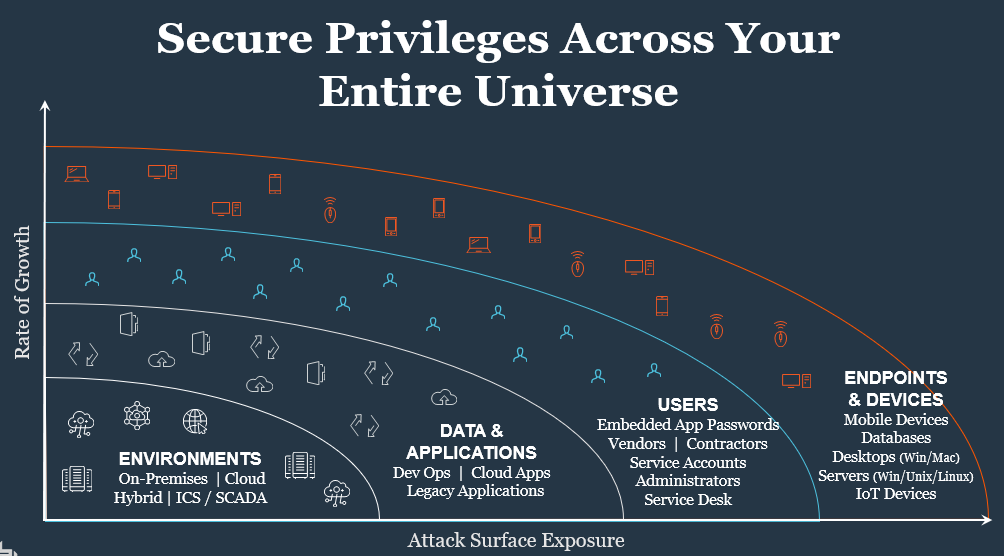
Med en nærmest eksplosiv vækst i antallet af privileged brugere på tværs af en infrastruktur, der for de fleste virksomheder er mere spredt og kompleks end nogensinde, så er det ikke længere nok med en basal kontrol med adgangsrettigheder og passwords.
Den voldsomt udvidede angrebsflade og de tilhørende risici fordrer en ny tilgang. Denne tilgang kalder BeyondTrust Universal Privilege Management.
Universal Privilege Management beskytter og styrer rettigheder for enhver bruger, enhver session, enhver asset/enhed .. og samler dit samlede rettigheds-univers for dramatisk reduktion af angrebsfladen og dermed din virksomheds cyber-risici.
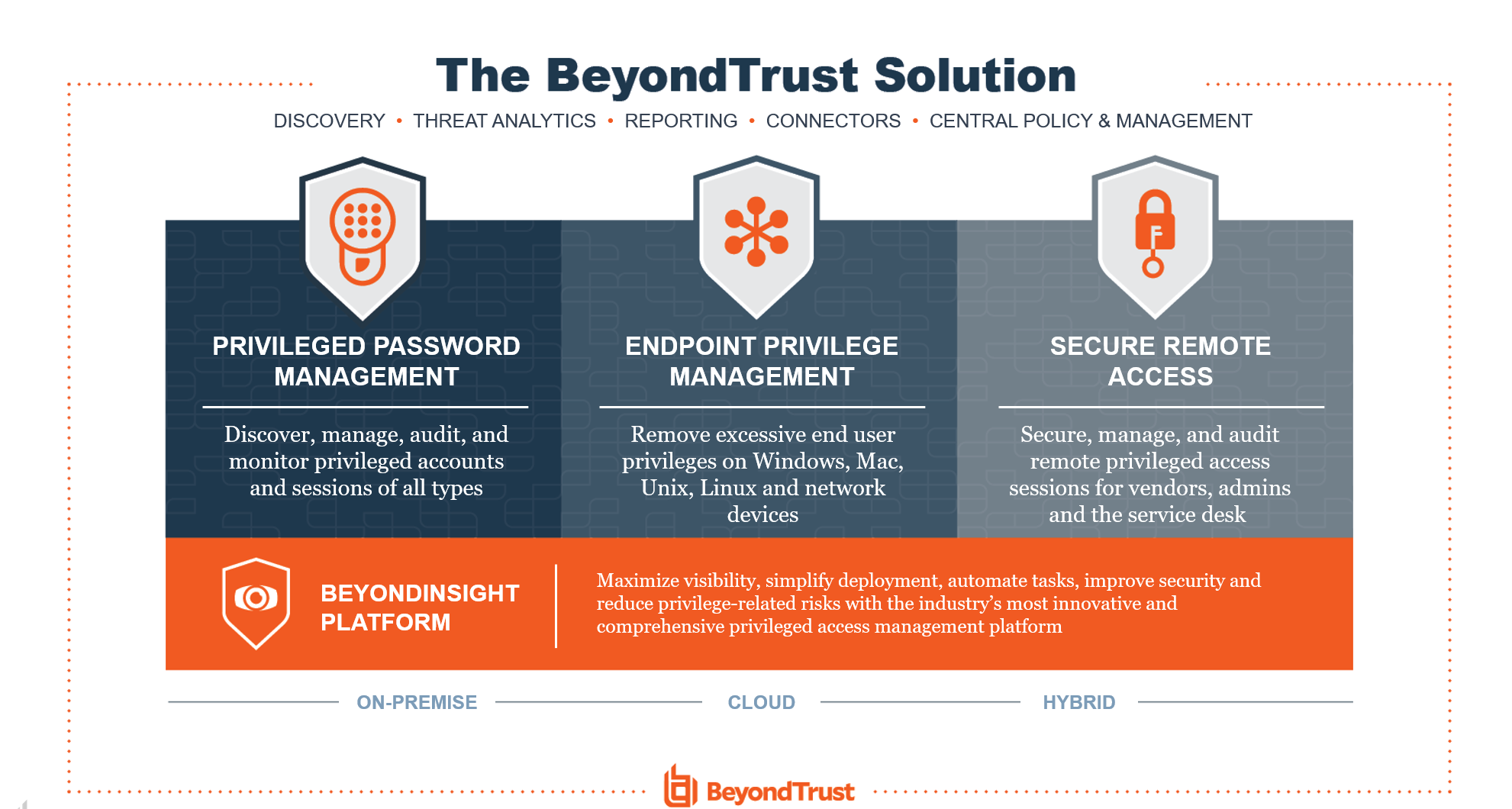
BeyondTrust Universal Privilege Management consists of three sub-elements:
- Privileged Password Management (also called Priviliged Account Management / PAM)
- Abuse of user rights is an important parameter in the majority of all cyber security incidents
- BeyondTrust is recognized as a market leader in PAM, and can meet virtually any need you may have in rights management
- Endpoint Privilege Management
- Stop attacks by removing extended privileges on Windows, Mac, Unix, Linux, and network equipment
- Secure Remote Access
- Superb control and security of remote access with i.a. full audit trail built-in, and with the highest level of flexibility for the business .. without the use of VPN
- Enables 3rd party / service technician remote access to e.g. OT infrastructure with ..
- Finger-granulated access control
- Full documentation of the technician’s work (audit & compliance)
- Support for proprietary protocols & platforms, e.g. OT development software and PLCs


