Integration between Cisco and partners like Nozomi Networks – what is it all about?
Nozomi has entered a collaboration with Cisco. This collaboration is established around different technologies that are developed by Cisco. These technologies are briefly described below. By clicking the link below, you can read more on Cisco’s possibilities of integration, and the many technical alliances that the company has established within the field of security:
https://www.cisco.com/c/m/en_us/products/security/technical-alliance-partners.html

Integrating Guardian in Cisco Catalyst 9300 switches
The Guardian software can be installed in the “container” which is available on the Cisco Catalyst 9300 Switch-series. The solution is, in this way, one of Cisco’s “DNA” (Digital Network Architecture), which enables clients to automate the implementation of Nozomi Networks’ solutions to Cisco Catalyst and Connected Grid Routers portfolios.
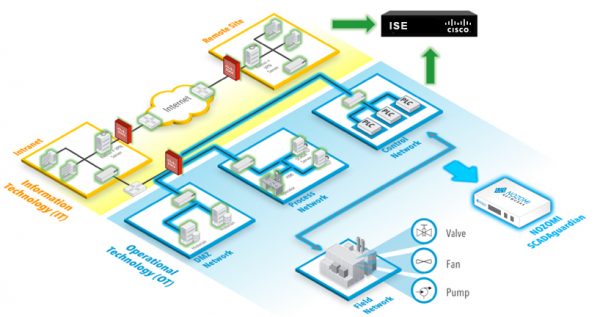
Cisco ISE – Access and privilege management in the ICS-infrastructure
This means that Nozomi’s Guardian and Cisco ISE (Identity Service Engine) can exchange data via PxGrid. This means that the following functions will be at your disposal if your company utilizes both Nozomi SCADAguardian and Cisco ISE in the production network:
- Cisco ISE provides further information for the “Asset view”, that Nozomi networks are managing. Correspondingly, ISE utilizes the information from SCADAguardian to develop stronger device profiles in Cisco ISE databases.
- Guardian delivers MAC: address information to Cisco ISE which allows for better possibilities for MAC-whitelists in ICS-networks
- SCADAguardian sends information to Cisco ISE who assists in changing policies for devices. Such as modifications in SGT (Security Group Tags), usage of ACLs to switch ports, altering VLAN, etc.

Cisco ASA/FTD – firewall – blokering af trafik eller “connections”
Fast response to network incidents is imperative, and Nozomi has taken steps to automate this reaction on cybersecurity incidents. Guardian can send information to Cisco ASA and Cisco Firepower Threat Defense (FTD) so that these firewalls can block outgoing communication from the ICS-infrastructure.
